FIDO2 provides a secure and modern way of performing authentication. Even government websites like ID-Austria have started using FIDO2 authentication for their online services. While most modern authentication works the same way, ID-Austria works differently.
FIDO2 provides a secure and modern way of performing authentication. Even government websites like ID-Austria have started using FIDO2 authentication for their online services. While most modern authentication works the same way, ID-Austria works differently.
What is ID-Austria
ID-Austria is the online authentication service used by many Austrian government websites and services. The registration requires a physical appearance at a “registration office” as well as two different devices to finish the online part of the registration while one device needs the “Digitales Amt” smartphone app and Biometric unlocking (fingerprint or face unlock) enabled. This seems to me overly complicated but is only required in that extent if no other online identification was used before. When registered, ID-Austria can be used to authenticate to many different government services. From social services to financial services, this authentication method is used to securely authenticate citizens to these websites. Additionally to the authentication using the ID-Austria smartphone App “Digitales Amt”, FIDO2 hardware security keys complying to their requirements can also be used to authenticate.
FIDO2 and ID-Austria
The Authentication service of ID-Austria is managed and operated by A-Trust. While ID-Austria is the branding used for this service, it is operated by A-Trust and as such, the browser might redirect to the A-Trust website and even show the A-Trust logo. To use a FIDO2 security key, the following requirements have to be met.
* FIDO2 hardware security key
* Webauthn supported
* FIDO2 Level 2 certified
While this seems relatively straight forward as FIDO2 already requires Webauthn support, Level 2 certified devices are not as common at the time of writing.
FIDO2 Level 2 hardware security key
One of the newest addition to the FIDO2 Level 2 certified hardware security keys is the Token2 Pin+ Release 3 devices. I am personally a fan of the Token2 PIN+ Dual Release 3 as they allow connecting to either a USB-C or a USB-A port without the need for an adaptor and support NFC connection as well. While the Token2 security keys are one of the cheapest on the market, they are also open-source hardware security keys (see Security keys and open source), manage to store an enormous 300 passkeys, provide all the FIDO2 (as well as FIDO2.1) features and also support additional features like TOTP (up to 50) as well as OpenPGP.
While testing the Token2 PIN+ Release 3 security keys provided to me by Token2, I had no issues registering and using them with any service or website. Sadly not something that can be taken for granted with some other brands I have tested.
FIDO2 registration with ID-Austria
While most services provide a rather common way of registering new authentication or multi factor authentication methods, ID-Austria does things differently. A usual approach to add a second factor method or an alternative login method is to let the user log in with their current login credentials and their already configured second factor, if any. After this authentication, the user can navigate to a section of the customer portal to add a security key. With ID-Austria, attempting to do so will end in frustration as it is not done this way.
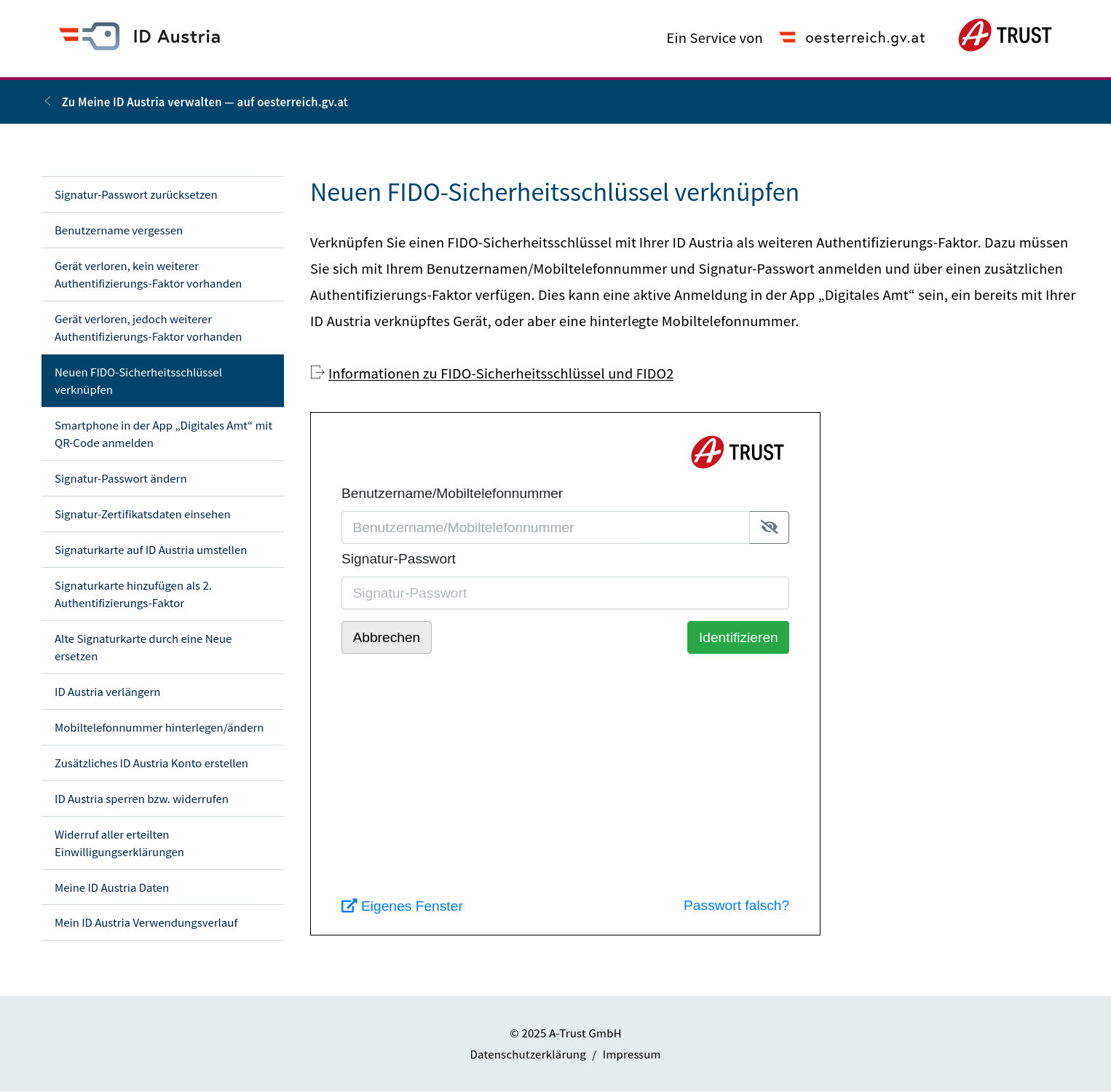
Instead, the user has to navigate to a specific URL https://www.oesterreich.gv.at/id-austria/Meine-ID-Austria-verwalten.html. The website opens without any form of authentication and offers options usually only expected after user authentication has succeeded. The list of options of the page contains blocking the ID-Austria account, changing the associated mobile phone number, signature password change and an option “Linking a new FIDO security key” (“Neuen FIDO-Sicherheitsschlüssel verknüpfen”).
When selecting the option “Linking a new FIDO security key”, the browser heads over to a-trust.at again to, well yes, authenticate first as there was no authentication so far.
To authenticate, any already setup authentication method can be used. If a security key is already set up, it can be used to authenticate here too.
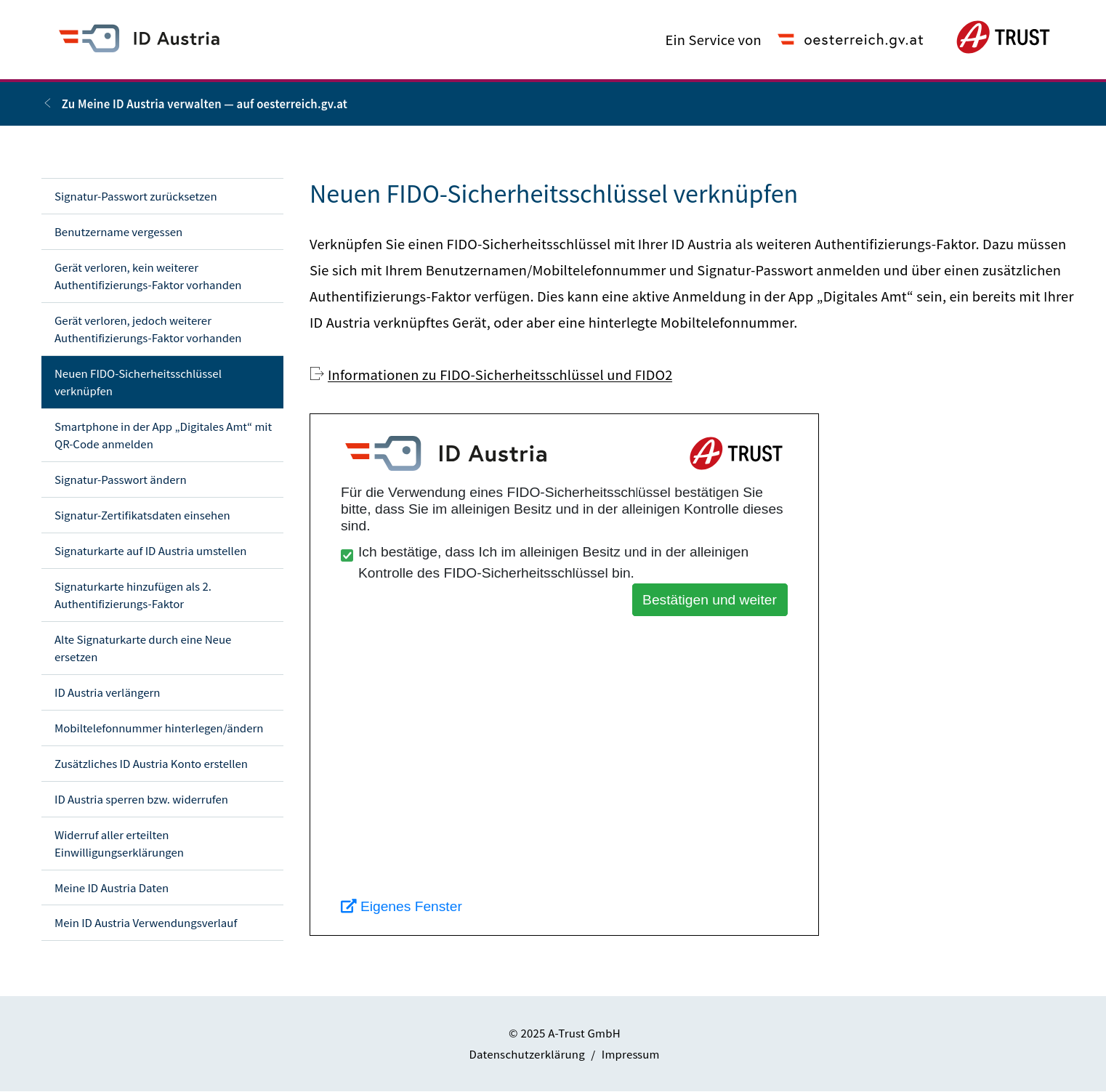
With the authentication step completed, the ID-Austria portal requests confirmation of ownership followed by an info screen with details about the next step of linking the hardware security key to the account. This is where the Level 2 security key, like the Token2 PIN+ Release3, should be connected.
After the info screen, the actual linking of the security key to the ID-Austria account is performed. Depending on the browser used (Chromium based or Firefox based) the screens and message look slightly different. Chromium based browsers seem to want to convince the user to use the App based Pass-Key authentication / registration and requires to explicitly select the hardware security key option. Firefox based browsers on the other hand simply trigger the authentication via the hardware security key.
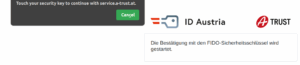
Follow the instructions shown in the browser and enter the PIN of the hardware security key and touch the sensor/touch-button to allow the creation of a FIDO2 credential on the hardware security key. To learn how to set a PIN, check out FIDO2 security key management via commandline.
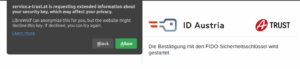
Another difference between the browser types is the request to share hardware security key details with the website. Firefox based browsers give users the option to “block” or “allow” the transfer of details about the FIDO2 security key. Chromium based browsers do not provide this option at all. As ID-Austria needs to verify a Level 2 certified security key is used, the request should be allowed.
Once the credential is created and the public key information has been transferred, the security key is linked.
At the time of writing, Token2 is one of the latest additions to the list of supported FIDO2 hardware security keys for ID-Austria. While writing this article, the Token2 PIN+ Release3 are already officially supported and working with ID-Austria / A-Trust – although the website does not yet list them as supported devices. I am confident, the details on the website will be updated soon to show the newly added Level 2 hardware security keys.
Disclamer
We would like to thank Token2 for providing the hardware security keys used in our testing. However, Token2 did not have any influence or control over the details and opinions expressed in this article. We found the collaboration with Token2 to be very productive, and we appreciate all their great support.
Read more of my posts on my blog at https://blog.tinned-software.net/.